Applications
We usually say that your application — a single application — communicates with Auth.it. However, this is not always the case in modern deployments. What appears to be a single application on the outside may actually consist of multiple applications, most commonly a backend and a frontend.
The Applications view in the Auth.it Dashboard helps you configure all applications in your deployment that use Auth.it for authentication. This enables your users to log in once and access both the frontend and the backend without re-authenticating.
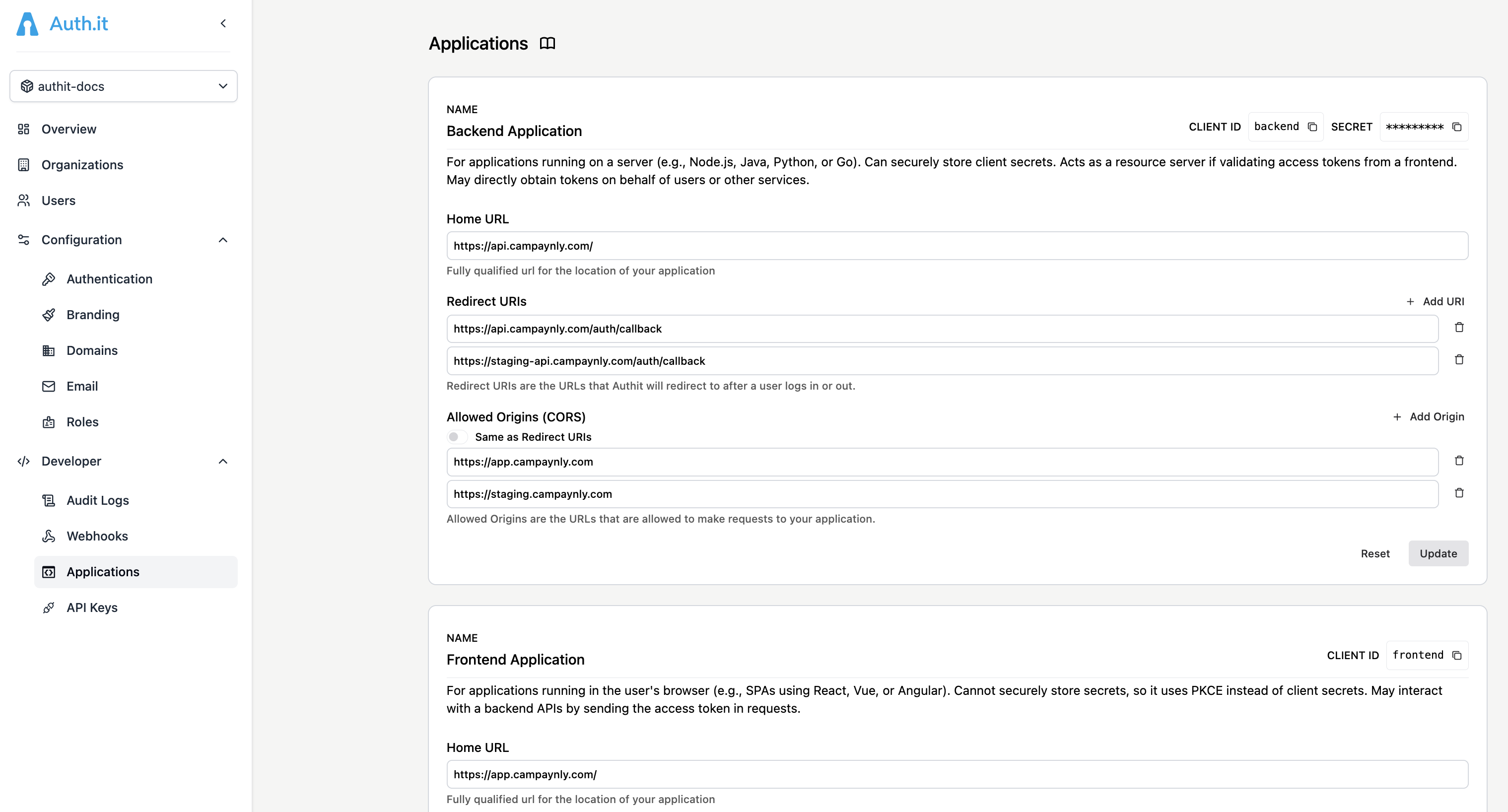
Each application you configure in Auth.it corresponds to an OIDC client — a connection that defines how one part of your system (such as a frontend or backend) communicates with Auth.it, including redirect URLs, allowed origins, and whether it uses a client secret.
You’ll typically have:
- A frontend client used to authenticate users in the browser.
- A backend client used by your server to validate tokens and access APIs securely.
OpenID Connect (OIDC) is an identity layer built on top of OAuth 2.0 that enables applications to authenticate users securely.
Instead of managing usernames and passwords yourself, you delegate authentication to an identity provider, which issues standardized tokens. These tokens contain information about the user (the ID token) and can be used to request additional resources with proper authorization (via the access token).
Built-in applications
Auth.it currently supports two built-in applications: Backend Application and Frontend Application.
Backend Application is intended for backend services of any type, where a client secret can be securely stored on your server. The client secret is generated automatically and can be copied from the top-right corner of the application’s settings pane.
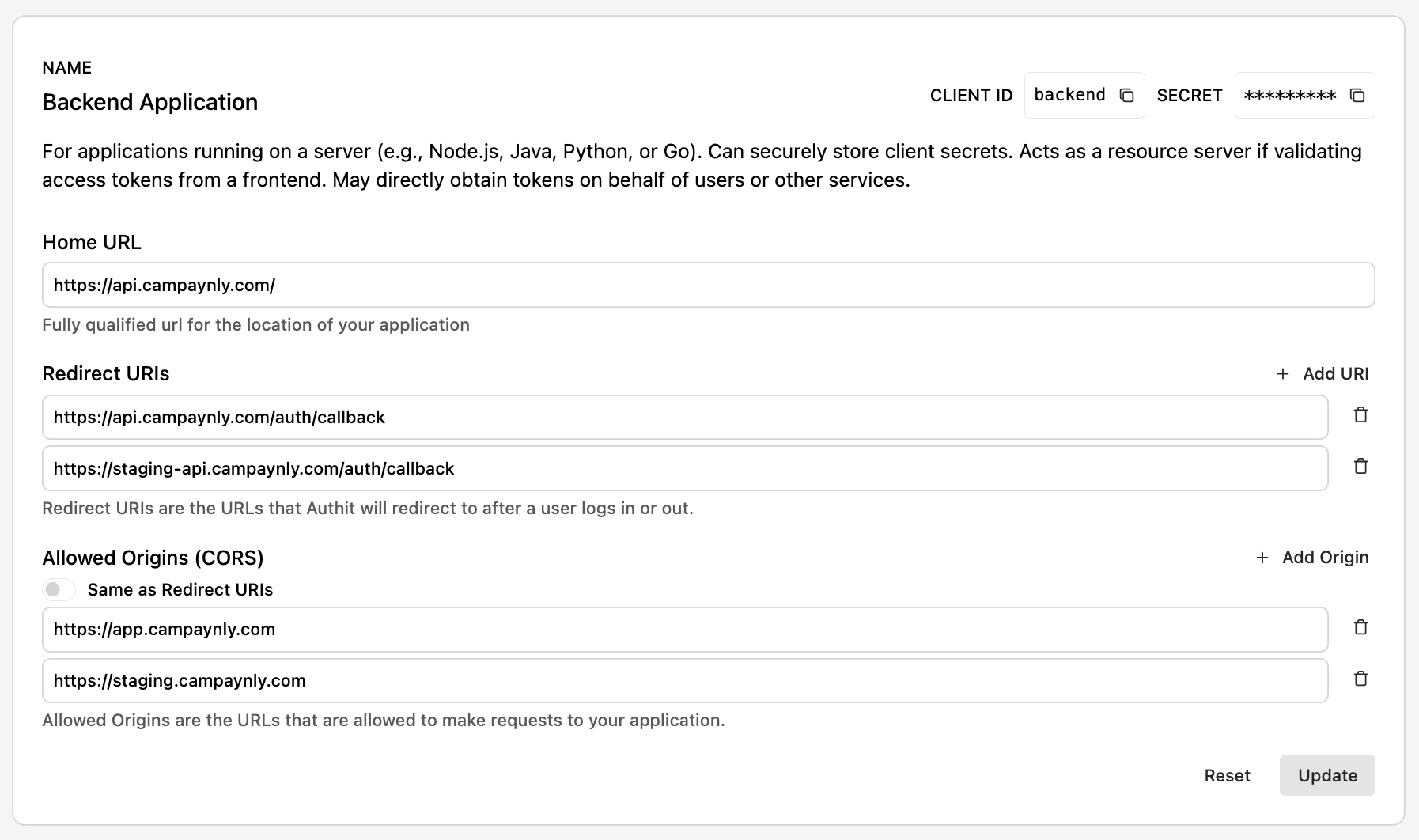
Frontend Application is designed for frontend or single-page applications (SPAs), where it is not possible to securely store a client secret. No client secret is generated in this case, and only a client ID is provided.
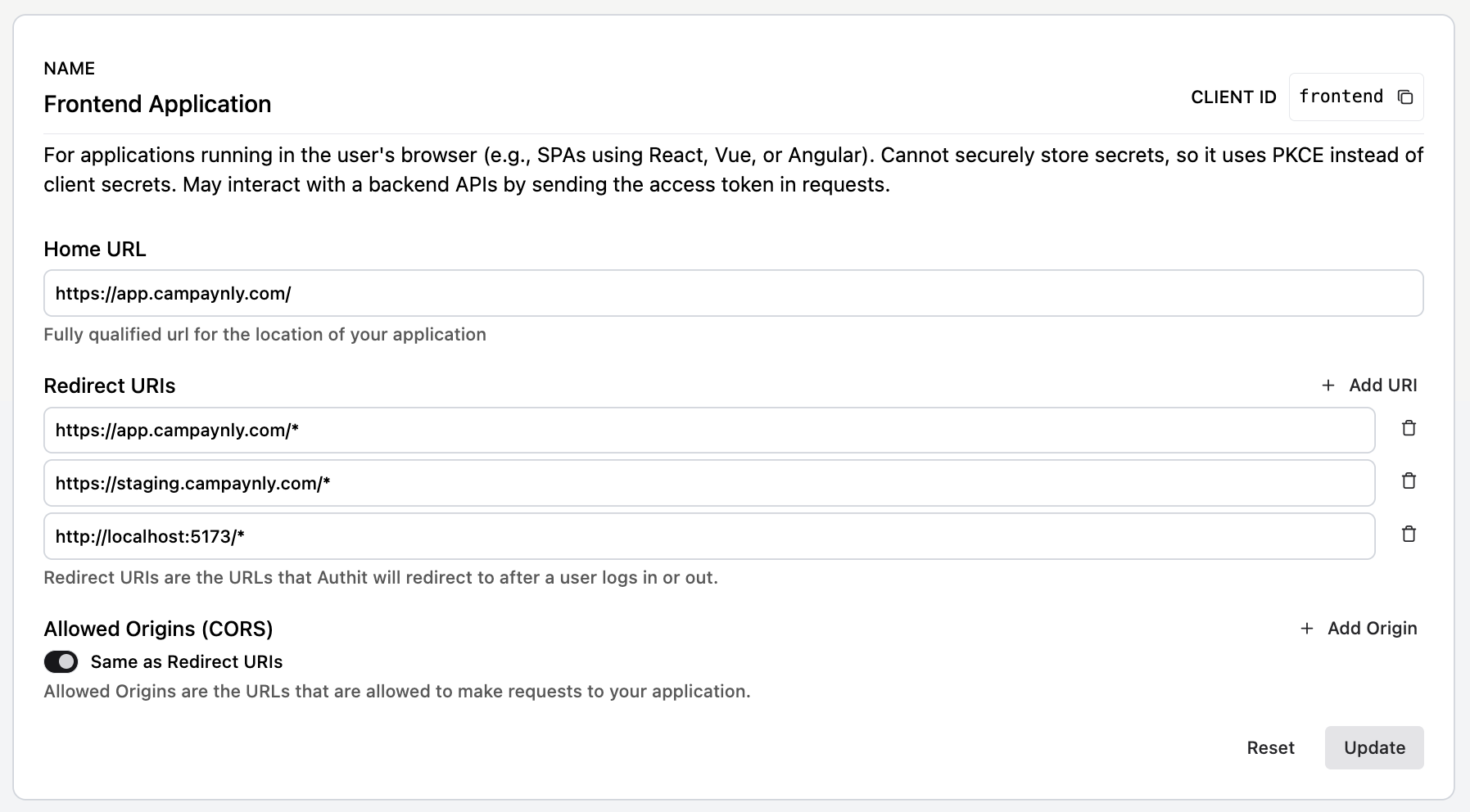
Each application has several parameters you need to configure:
- Home URL: the default URL used when Auth.it needs to redirect or link back to the client. This value is ignored if a specific redirect URI is provided in the request.
- Redirect URIs: the callback endpoint(s) in your application where Auth.it sends users — along with their authorization tokens — after successful login. You can use wildcards at the end of the URL pattern (for example,
https://host.com/path/*). A full wildcard*is also supported, allowing any HTTP or HTTPS redirect URI. However, avoid using full wildcards in production — specific redirect URI patterns are much more secure. - Allowed Origins (CORS): a list of domains allowed to make JavaScript requests directly to Auth.it endpoints. Limiting allowed origins helps protect against XSS, CSRF, and other JavaScript-based attacks. For convenience, you can set this to the same values as your redirect URIs using the toggle in the form.